Introduction
This topic describes the Identity service provided by the ZAN system. Identity is an online e-KYC solution for proving "who you are" on the internet based on ID documents and face recognition.
Identity collects user ID pictures and selfie images, and compares them to detect if they are of the same person for the online verification of users' real identities. During this process, Identity helps you to detect whether there are forged documents and if the face captured is genuine to ensure the authenticity and accuracy of the information submitted by the user.
Features
Document capture
Document capture captures the users’ ID picture, and the algorithm will check the quality of the captured picture as well as verify whether it is the specified ID type.
Identity provides two capture methods: automatic capture and manual capture.
- Automatic capture (recommended): The algorithm automatically determines whether the picture is clear. When an eligible ID picture is detected, the algorithm will automatically capture and upload it. This capture process does not require the user to tap on the screen.
- Manual capture: Users will need to manually tap the capture button and confirm whether the picture is clear enough.
Document anti-spoofing
The document anti-spoofing detection captures and analyzes the document image to determine whether it is a genuine document and if there is a fraud risk i.e. photo prints, screen remakes, or masks. For specific ID card types (e.g. Hong Kong China ID card, Malaysia ID card), Identity also supports security feature checking to determine whether the document is a high-quality imitation.
Document OCR
Document OCR (Optical Character Recognition) supports structured recognition of key fields on a document, such as the document number, name, date of birth, and more.
Face capture
Face Capture captures users’ live selfie images. The user cooperates by lifting the phone and facing the screen, then follows prompts such as blink/performing other actions so that a selfie image of their face can be captured and collected through the front camera. The algorithm will automatically determine whether the user’s face is genuine and whether the quality of the selfie image is acceptable.
Liveness detection
By capturing and analyzing face images, Identity determines whether it has collected a real face, or a photo or video. Identity provides a variety of image algorithm capabilities for liveness detection, and it can help you to identify and defend against presentational attacks such as 2D images, screen remakes, 3D masks, and more. It can also combine multi-frame image and anti-spoofing algorithms to identify injection attack, before finally completing the face capture process.
Face compare
Compares the collected ID portrait with the selfie image to determine if the two faces belong to the same person.
Risk control system
Identity has a risk control engine to determine the risk strategy. Risk control is mainly reflected in the following two aspects:
- The initialization session before starting image capture
Identity will determine whether the same device or the same user IDs has displayed multiple risk behaviors within a short period of time. For example, attempting multiple photo attacks. When the number of retries exceeds the limit, the system will reject the initialization request. A new Identity session can only be started again after a certain period of time. - Processing session after successful image upload
Identity will determine whether the same ID number or the same face has displayed multiple risk behaviors within a short period of time. For example, attempting multiple photo attacks, or multiple comparison failures etc. When the number of retries exceeds the limit, the system will consider it risky and return either Pending or Failure as the final business result.
Use flow
The use flow of Identity is shown below:
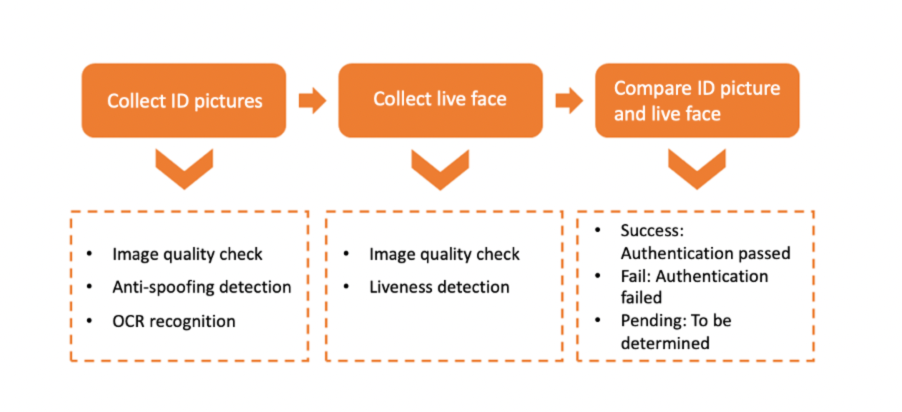
- Capture an ID picture.
The user prepares their ID document to be photographed and aligns it with the frame guide box in the capture interface. They will then take a clear and complete photo of the ID document. Identity supports 2 ways for users to capture their ID documents: automatic capture and manual capture.Note: The user experience for automatic capture user experience is better. Users can capture more image data, which is convenient for more advanced document anti-spoofing detection as the anti-spoofing protection is stronger. It is recommended for users with anti-spoofing needs to choose the automatic capture method.- Automatic capture (recommended): The algorithm automatically determines whether the photo is clear, and the user will be prompted to adjust the document in real-time if the quality of the ID picture is inadequate during the capture process. When an eligible ID picture is detected, the algorithm will automatically capture and upload it. This capture process does not require the user to tap on the screen.
- Manual capture: Users manually click the capture button and confirm whether the photo is clear enough. If the algorithm determines that the quality of the uploaded photo is inadequate, a pop-up box will appear and prompt the user to re-capture, as shown in the following figure.
- Capture a live face.
Users will need to raise their phone and face the screen. They will have to follow the prompts given and complete certain actions i.e. blinking/other actions, as well as take a selfie using the front camera. The algorithm will automatically determine whether the face captured in the selfie is human, and whether the quality of the face capture is acceptable.- When an eligible selfie image is detected, the algorithm will automatically capture and upload it. This capture process does not require the user to tap on the screen.
- If the algorithm detects that the quality of the selfie is inadequate, it will guide the user to adjust their phone with corresponding prompts, such as if they should move closer or further, if their face needs to be better lit, etc. To verify that it is indeed a genuine human face in front of the camera and not a photo, the algorithm will ask the user to perform an action such as blinking. The capture process will only be successful when the prompted action has been performed.
- The collected ID portrait and selfie image are compared to determine if the two faces belong to the same person. When the ID portrait and the selfie image have been uploaded successfully, Identity's server will automatically conduct a face comparison. The final result will then be returned to the user in the form of success/pending/fail.
Contact Us
Learn more about the Identity product and access solutions by contacting us: [email protected].
Updated about 1 month ago
