👷 Security Settings
You can configure security settings for your API key, including secret-based two-factor authentication on connections, the contract address allowlist, the source allowlist, the API request method allowlist, and the upper limit of credit consumption.
Overview
Priority: security protection.
In this chapter, you will be able to configure the following security Settings:
- Secret-based two-factor authentication
You can enable secret-based two-factor authentication to ensure access security. - Allowlist control
- Contract address allowlist: You can limit the accessible contract addresses to prevent abuse of API keys.
- Source allowlist: You can control the source IP addresses from which access requests can be initiated.
- Credit usage control
- You can implement fine-grained control over the methods that can be called by using an API key.
- You can set the upper limits of credit usage for API keys.
Configuration path
- Log in to the ZAN Node Service Console and click on Chain RPC in the left navigation bar.
- Switch to the Security tab, where you can configure the settings to secure API key-based connections.\
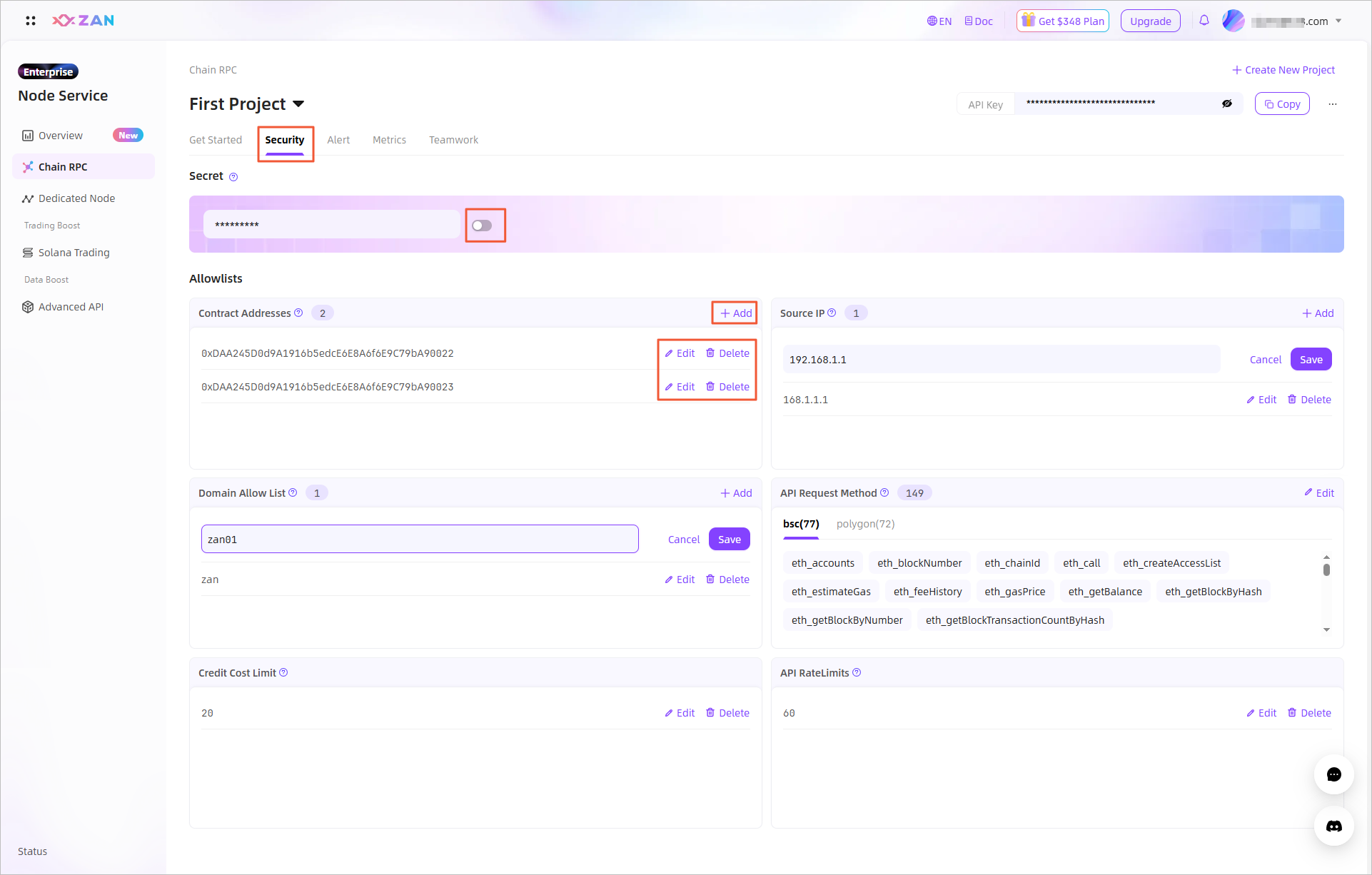
You can configure the following settings to secure API key-based connections:
Configuring secret-based two-factor authentication
By default, the system generates a secret for two-factor authentication for your API key. You can enable the secret to enable two-factor authentication, which can ensure access security.
- Enable the secret.
If the secret is disabled, toggle the switch on the right side of Secret. After your confirmation, the secret-based two-factor authentication feature is enabled for your API key. After the secret is enabled, all requests must undergo two-factor authentication by using the secret. The system allows access only after the authentication succeeds. - Disable the secret.
If the secret is enabled, toggle the switch on the right side of Secret. After your confirmation, the secret-based two-factor authentication feature is disabled for your API key. After the feature is disabled, the system no longer uses this secret to perform two-factor authentication on subsequent requests.
Setting a contract address allowlist
You can configure a contract address allowlist to limit the accessible contract addresses to prevent the abuse of your API key.
If your application only queries data from specific Ethereum smart contracts or addresses, add those addresses to the contract addresses allowlist.
Any requests which query addresses that are not in the allowlist are rejected.
The following RPC methods take an Ethereum address parameter and are compatible with type of allowlisting:
- eth_call
- eth_estimateGas
- eth_getLogs
- eth_getBalance
- eth_getCode
- eth_getStorageAt
- eth_getTransactionCount
In the Allowlists module, add contract addresses in Contract Addresses to configure the allowlist.
- If no contract addresses are specified in the contract address allowlist, the allowlist is disabled by default and all contracts are accessible.
- After you add contract addresses to the contract address allowlist, only contracts with the specified addresses can be called by the API.
- To add contract addresses, click on the input box, specify one or more contract addresses, and then click Save.
- To modify the contract address allowlist, click on the input box, delete existing contract addresses as needed, and then click Save.
Setting a source allowlist
You can configure a source allowlist to specify the IP addresses that can be used to initiate access requests.
In the Allowlists module, add IP addresses in Source IP to configure the allowlist.
- If no IP addresses are specified in the source allowlist, the allowlist is disabled by default and access requests from all IP addresses are allowed.
- After you add IP addresses to the source allowlist, only requests from the specified IP addresses are allowed.
- To add a contract address, click the Add button at the top right corner of the Contract Addresses form, then click Save when finished.
- To modify a contract address, click the Edit button on the right side of the target row, and then click Save.
- To Delete a contract address, click the Delete button on the right side of the target row and confirm the action.
Setting a domain allowlist
You can configure the domain addresses that are accessible by this API key. After configuration, when you make API requests using clients (such as Postman, SDK, or wallet apps), you need to pass the corresponding field value that conforms to the domain setting in the "Origin" field of the Headers. The specific correspondence is as follows.
| Origin value | Domain allowlist in ZAN | Allowed |
|---|---|---|
<empty>, <anything> | [] | ✅ |
zan.top | ["zan.top", "\*zan.top", "zan.top*"] | ✅ |
zan.top | ["zan"] | ❌ |
zan.top | ["*.zan.top"] | ❌ |
www.zan.top | ["\*.zan.top", "\*zan.top", "\*zan.top*"] | ✅ |
<empty> | ["zan.top"] | ❌ |
In the Allowlists module, add the domain addresses in the Domain Allow List to restrict access for the current API Key. It supports configuring multiple domain whitelists and also supports wildcard format, such as "**@zan.top".
- If no domain addresses are specified in the domain allowlist, the allowlist is disabled by default and all domain addresses are allowed to be accessed when making API requests.
- After you add specific domain addresses in the domain allowlist, Only the specified domain addresses can be accessed by using this API key.
- To add an IP address, click the Add button at the top right corner of the Source IP form, then click Save when finished.
- To modify an IP address, click the Edit button on the right side of the target row, and then click Save.
- To Delete an IP address, click the Delete button on the right side of the target row and confirm the action.
Setting an API request method allowlist
You can configure an API request method allowlist to implement fine-grained control over the methods that can be called by using an API key.
In the Allowlists module, add specific API request methods in API Request Methods to configure the allowlist.
- If no API request methods are specified in the API request method allowlist, the allowlist is disabled by default and all API request methods can be called.
- After you add API request methods to the API request method allowlist, only the specified API request methods can be accessed by using this API key.
- To add API request methods, click the Edit button on the top right corner of the API Request form, specify one or more API request methods, and then click Save.
- To modify the API request method allowlist, click the Edit button on the top right corner of the API Request form, delete the existing API request methods as needed, and then click Save.
Setting the creditt cost limit
You can configure the upper limit of credits that can be consumed for an API key to implement control over credit usage.
In the Allowlists module, specify the maximum number of credits that can be consumed in Credit Cost Limit to configure the upper limit of credit usage.
- If you do not configure an upper limit, the system does not reject the requests to this API even when an excessive number of credits are consumed.
- After you configure the upper limit, the system rejects the requests to this API when the upper limit is reached.
- To configure the upper limit of credit usage, click the Edit button on the Credit Cost Limit form, specify an upper limit, and then click Save.
- To modify the upper limit of credit usage, click the Edit button on the Credit Cost Limit form, specify another upper limit, and then click Save.
- To Delete the upper limit of credit usage, click the Delete button on the Credit Cost Limit form and confirm the action.
Setting the API RateLimits
You can configure the maximum Rate that can be used with this API key to implement control over credit usage per second.
In the Allowlists module, specify the maximum number of credits that can be consumed per second in API RateLimits to configure the upper limit of credit usage per second.
- If you do not configure an upper limit, the system will be restricted according to the current plan's ratelimits.
- After you configure the upper limit, the system rejects the remaining API requests when the upper limit is reached.
- To configure the API RateLimits, click the Edit button on the API RateLimits form, specify an upper limit, and then click Save.
- To modify the API RateLimits, click the Edit button on the API RateLimits form, specify another upper limit, and then click Save.
- To Delete the API RateLimits, click the Delete button on the API RateLimits form and confirm the action.
Updated 4 months ago
