Seeking Helsings FAQ
How can I participate in the event?
The Seeking Helsings event consists of two tracks: the Contract Security Track and the System Security Track. Users can choose to participate in either track or both. Detailed participation rules for each track can be found on the event page.
How do I submit a vulnerability?
- Click the Submit report button on the event page, which will redirect you to https://mysrc.group/project_hall. Select the relevant track: either the Contract Security Track or the System Security Track, and click to enter the project details page.
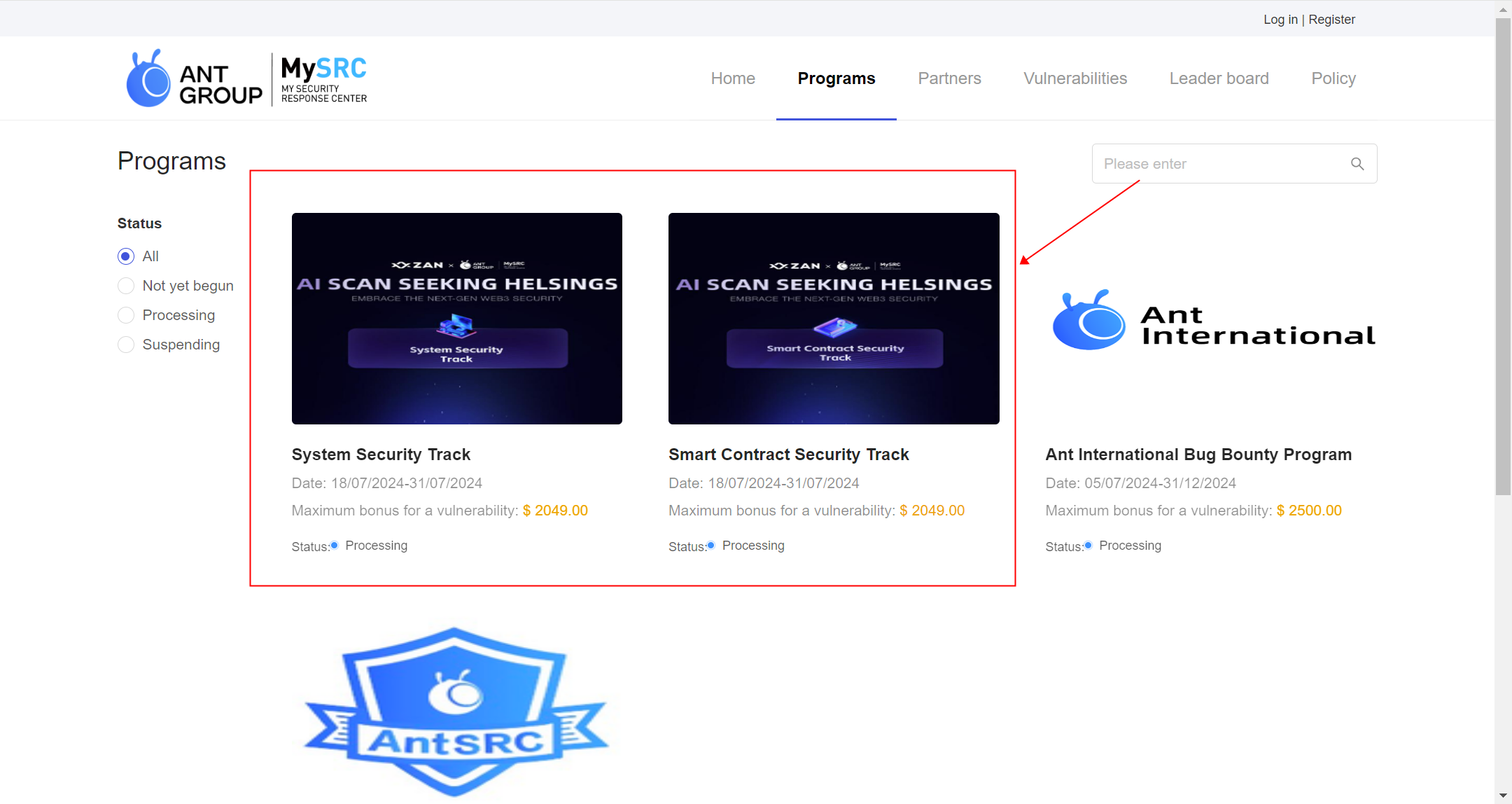
- Click the "Submit Report" button.
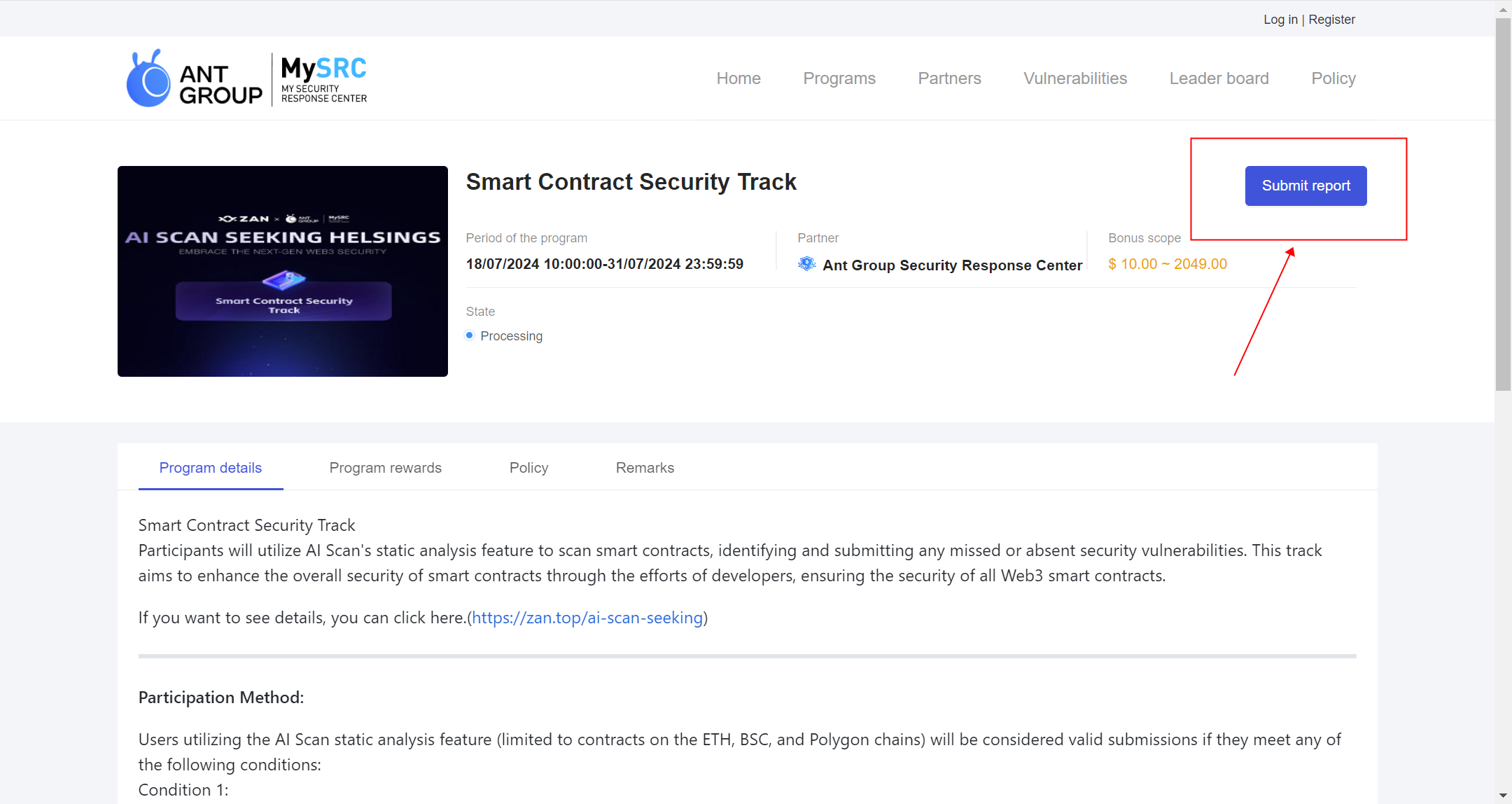
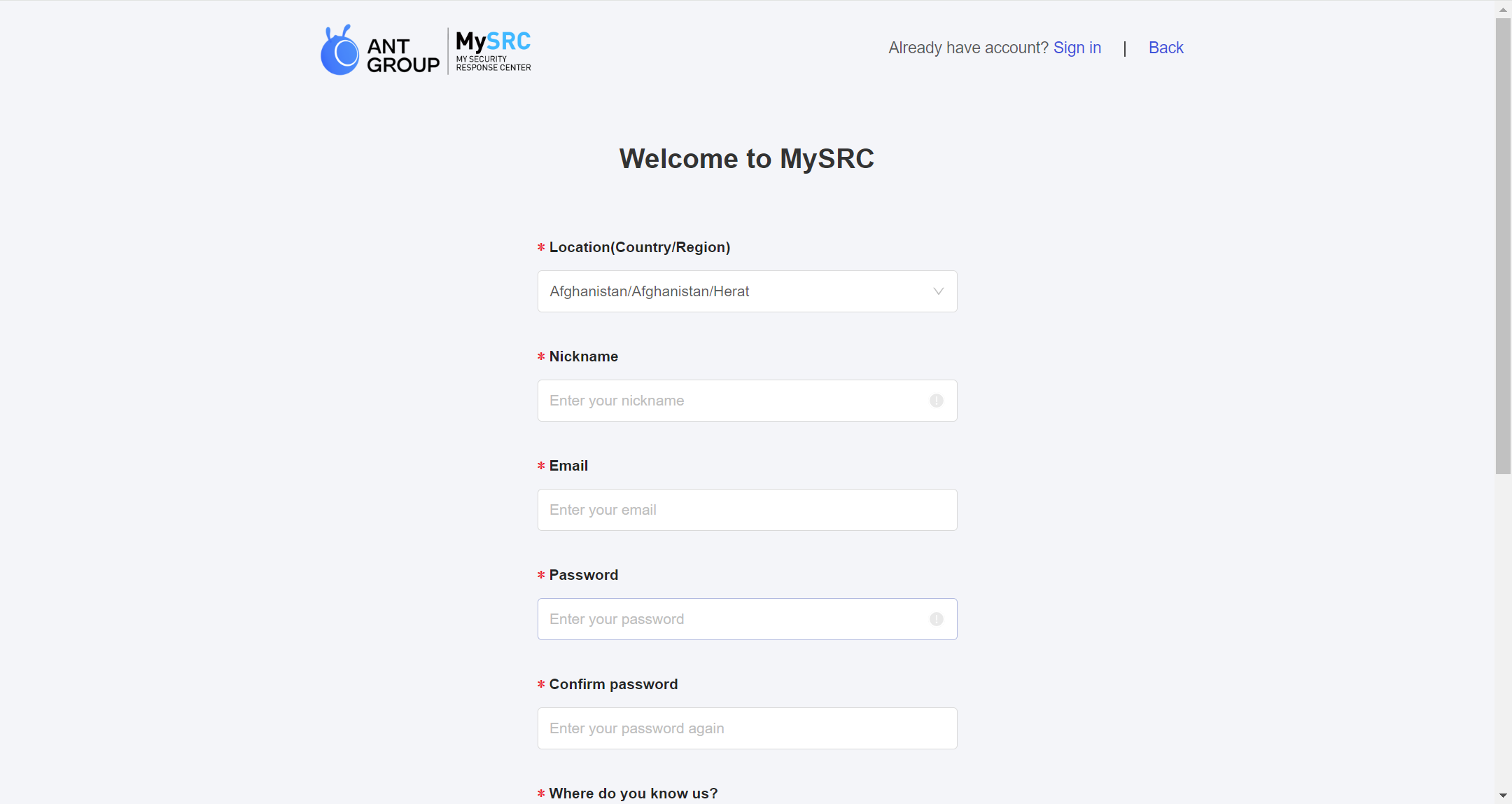
- Unregistered users need to complete the registration process; registered users need to log in.
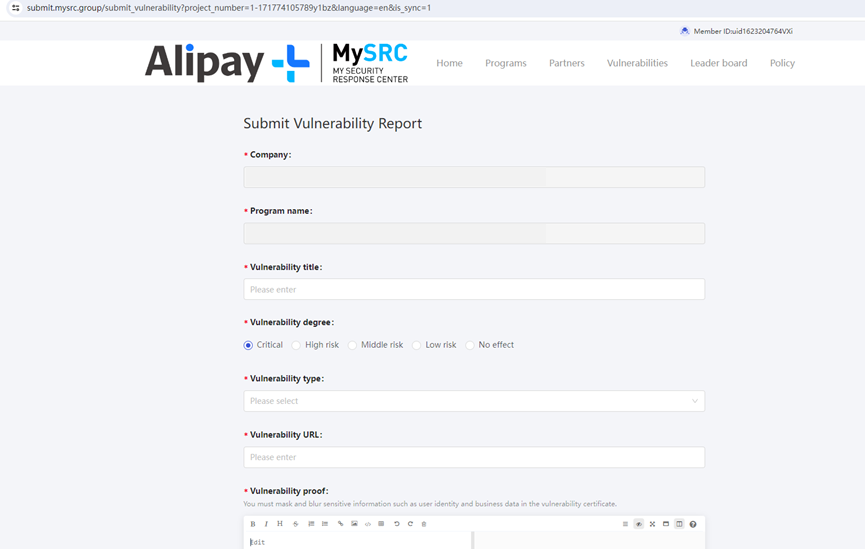
- Fill in the report details (refer to the event page for specific submission requirements for each track).
- ZAN official personnel will review the report, and valid vulnerabilities will be rewarded.
How are vulnerabilities classified?
For the Contract Security Track
Participation Prize
- Condition 1: False positives detected by tools with rule levels classified as Medium and Low will receive a Participation Prize.
- Condition 2: Submission of missing rules for rule levels classified as Medium and Low will receive a Participation Prize.
Security Prize
- Condition 1: False positives detected by tools with rule levels classified as High will receive a Security Prize.
- Condition 2: Submission of missing rules for rule levels classified as High will receive a Security Prize.
Helsing Prize
- Combined Conditions: The participant with the highest number of valid submissions, meeting either Condition 1 or Condition 2, will receive the Helsing Prize. (In the case of multiple participants having an equal number of submissions, the prize will be equally divided.)
Explanation of Contract Rule Levels:
- High Risk: Vulnerabilities at this level may adversely impact the confidentiality, integrity, availability, or economic model of the smart contract. This may lead to substantial economic losses, large-scale data issues, privileged access breaches, critical function failures, reputation damage, or disrupt the normal operation of other interacting smart contracts, resulting in considerable losses and irreversible damage.
- Medium Risk: Vulnerabilities at this level may negatively affect the confidentiality, integrity, availability, or economic model of the smart contract, causing moderate economic losses, partial function unavailability, and reputation damage.
- Low Risk: Vulnerabilities at this level may have a minor impact on the smart contract, potentially posing security threats to the contract's business system, and requiring improvements.
For the System Security Track
High risk
- Vulnerabilities that can lead to escalation of privileges on core servers, including but not limited to memory corruption, WEBSHELL upload, remote code execution, etc.
Note: core servers refer to those storing information of funds, IDs and transactions. - Core sensitive information leakage vulnerabilities, including but not limited to those caused by loose permission control.
- Logic vulnerabilities of the core business that can be massively leveraged to cause the losses of both companies and normal users, including but not limited to account credential checking logic, data verification logic of core APIs, payment logic, etc.
- SQL injection flaws that can directly execute the command; Sensitive information leakage caused by SQL injections on core databases etc.
- Vulnerabilities of core business that can be triggered without interaction, such as stored XSS, file traversal and remote DoS attack caused by improper parameter handling.
- Logic vulnerabilities of the core business that can be massively leveraged to cause the losses of both companies and normal users.
Medium risk
- Security vulnerabilities that can only be triggered in an interactive approach, including but not limited to reflective XSS, JSON hijacking, CRLF and sensitive CSRF operations, etc.
- Leakage of general information, such as mobile phone numbers, personal names and transaction numbers.
- Remote Denial-of-Service vulnerabilities, including but not limited to DoS caused by attacking APIs, web pages and other components.
- Ordinary business logic vulnerabilities, including but not limited to leakage issues caused by exporting components or wrong access control, and redirection vulnerabilities.
- Stored XSS meeting any of the following conditions: 1) can only impact limited users; 2) cannot provide entry points; 3) the victim domain has set httponly flag.
- Business security problem with general risks, including cheating in promotion events or bypassing business policies.
- Ordinary databases (only containing business data. User IDs, funds and transaction information are excluded.)
Low risk
- Vulnerabilities that acquire user information under the special condition, including but not limited to reflected XSS or stored XSS on designated browsers.
- Information leakage that has low influence, such as the physical path of the server, phpinfo outputs, unimportant system files and logs of the local environment.
- Local Denial-of-Service vulnerabilities, which exist in PCs, local components of the mobile clients and processes.
- Vulnerabilities that are very difficult to exploit, such as MITM attacks and vulnerabilities in need of continuous interactions with users.
- Business security issues with low risks, including malicious registrations, business policies bypassing, cheating in business and cashing out behaviors, etc.
When will I receive the reward?
The event will be held from 2024.7.18 to 2024.7.31, with the evaluation period from 2024.8.1 to 2024.8.14. Rewards will be issued to the bank account provided by the user within 30 days after the evaluation period ends.
Updated about 1 month ago
